Solutions & Technologies
Threat Detection and Mitigation
Effectively stop attacks with AI and automation
Juniper security services use AI and automation to accurately predict attacks and stop them before they’re successful with industry-leading efficacy. Filter and control applications, thwart exploits and malware, dynamically detect zero-day threats, and stop lateral movement and DDoS attacks without unduly impacting end users.
Leverage contextual threat intelligence to operationalize security so the entire network comes to its own defense, accelerating attack detection and mitigation, and freeing up network resources and your team.

99.9% Security Effectiveness
Juniper received an “AAA” rating in CyberRatings’ 2023 Enterprise Network Firewall Report, demonstrating a 99.9% exploit block rate with zero false positives.
How Juniper can help
Security should be built into the DNA of the network to eliminate attack vectors and unintentional gaps in defense—and it should be effective. Juniper has the most effective threat protection in the industry, extending threat intelligence and enforcement to all points of connection on the network to detect and block exploits, malware, ransomware, botnets, and distributed denial-of-service (DDoS) attacks. Further mitigate risk with unified policies that follow applications as they move between your data center and the cloud and use endpoint profiling to put control of compromised devices back in your hands.

Eliminate Patient Zero
Effectively predict and prevent both known and zero-day threats at line rate using the power of AI, before they cause infection. Protect your network for the entirety of the attack lifecycle, including both initial and subsequent attacks.

The industry’s most effective security
Juniper security services have been proven to be the most effective against threats for the past four years by multiple objective third-party tests.

Build a threat-aware network
Effectively secure users, data, and infrastructure without additional overhead, consistently across all architectures. Extend threat intelligence to the rest of the network, turning routers, switches, and access points into security sensors and enforcement points.
CUSTOMER SUCCESS
Pac-12 Builds All-Star Network to Better Serve Sports-Hungry Fans
The Pac-12 has won more NCAA championships for team sports than any other conference, and millions of fans watch basketball, soccer, football, and other college sports from Pac-12 Networks. To ensure operational simplicity and easy scalability of its digital and TV broadcast operations, the media company of the Pac-12 adopted an all-Juniper network connecting its data center to 116 college sports venues.

Resource Center
Practical Resources
Trials
Support
Training & Community
Background Information
Industry Recognition
Learn More
Blogs
Video
Discover 283% ROI with Juniper Connected Security
Live Events and On-Demand Demos
Threat Detection and Mitigation FAQs
What is threat detection and mitigation?
Juniper provides threat detection and mitigation services to find and block known and zero-day cybersecurity threats using several Juniper products and solutions:
- Juniper Security Director
- Secure Analytics SIEM
- Juniper Advanced Threat Prevention
- Juniper Next-Generation Firewall Services
- Security Intelligence (SecIntel)
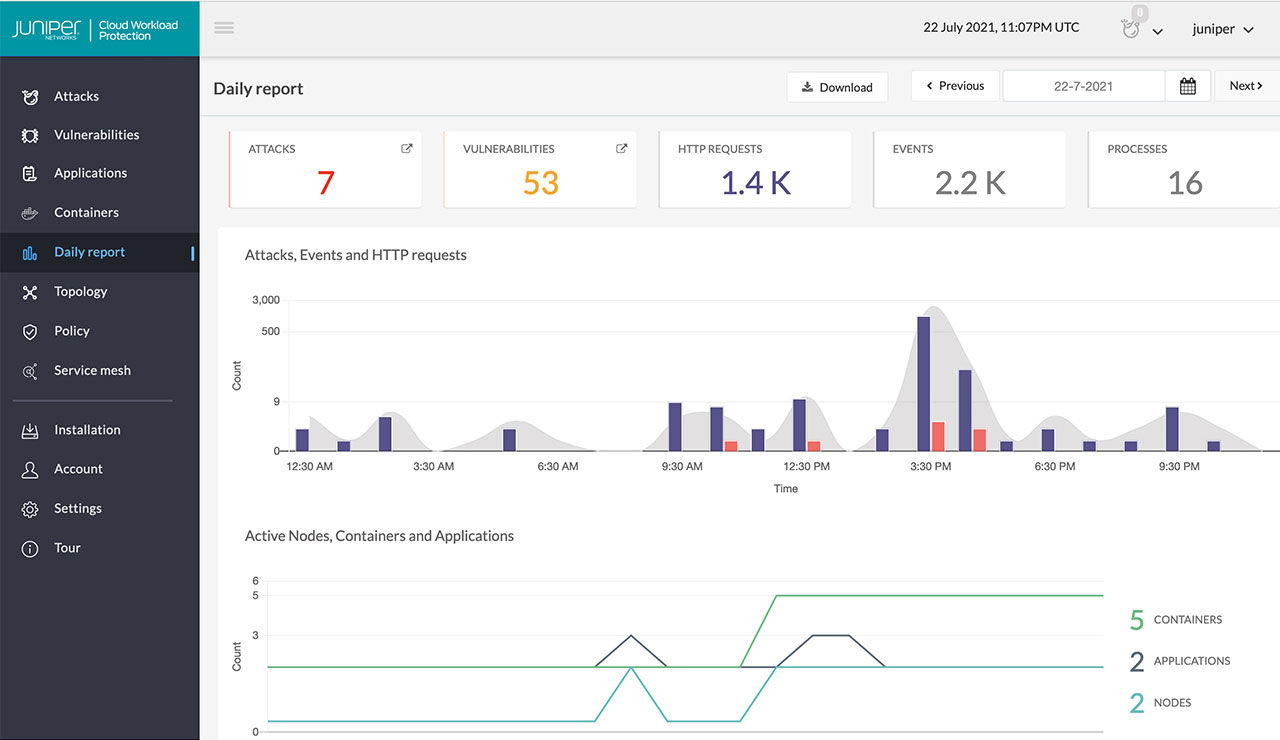
- Juniper Cloud Workload Protection
What are the benefits of Juniper Threat Detection and Mitigation solutions?
Juniper Threat Detection and Mitigation solutions offer several benefits, including:
- Leveraging analytics to identify trends on the network to help diagnose and mitigate threats
- Unbroken visibility across the entire network so you can see activity as it happens
- Stopping malicious outbreaks using curated, consolidated, and actionable intelligence to halt them in their tracks before they start moving laterally and wreak havoc on your network
- Automating critical, repetitive processes to simplify your security team’s workload and allow them to focus on strategic tasks
- Preventing threats that target difficult-to-secure Internet of Things (IoT) devices, such as coffee makers and printers, from taking down your network
Who should deploy Juniper Threat Detection and Mitigation solutions?
Juniper Threat Detection and Mitigation solutions are ideal for a wide range of organizations across various industries. They are particularly suitable for organizations that:
- Are looking to identify and block known and unknown threats
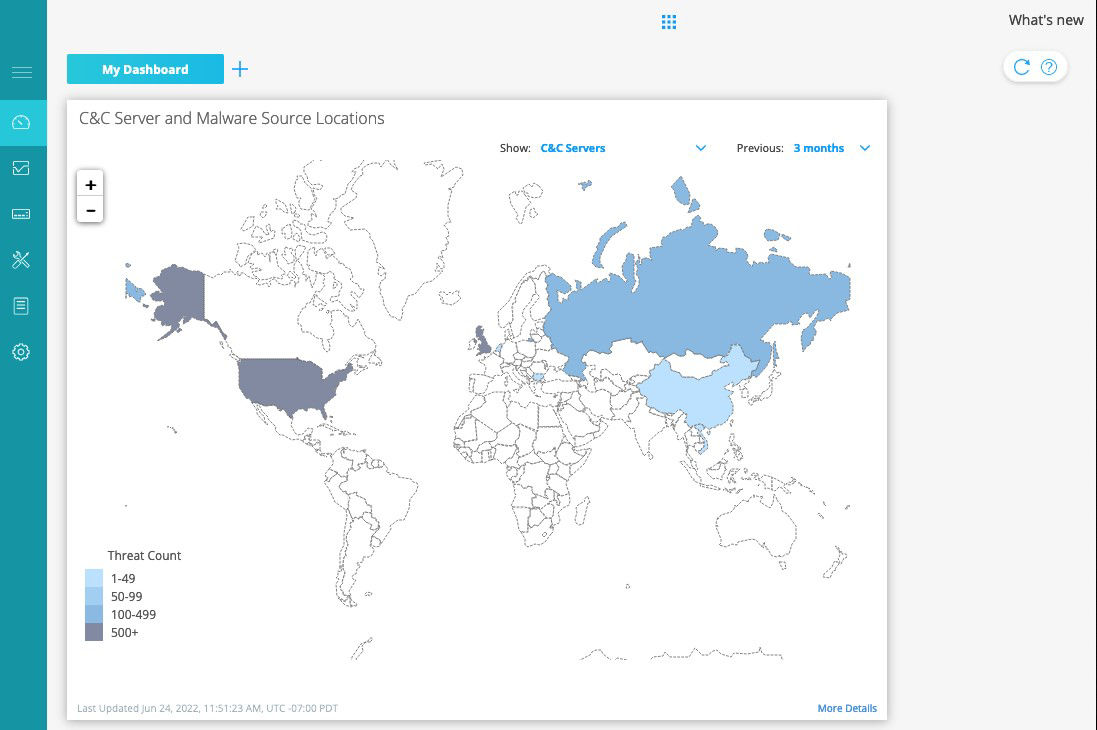
- Are looking to uncover zero-day malware threats and malicious connections, including botnets and C&C servers hiding in encrypted traffic
- Require threat prevention from web and email-borne attacks
- Want advanced artificial intelligence (AI), machine learning (ML), static, and behavioral analysis of files
- Require analysis of DNS traffic to protect against threats using DGA and DNS tunneling to hide communications and exfiltrate data from protected resources
- Are looking to better manage the growing number of IoT devices on the network and an easier way to identify and create policies across enforcement points on the network
- Want to leverage a cloud-based platform for resiliency, scalability, and centralized management of their threat prevention solution
- Require an on-premises solution to address security policy requirements for air-gapped environments
- Want the benefit of a threat-aware network based on threat prevention services shared across enforcement points that orchestrate security intelligence
- Need to block known and unknown threats off the network for the entire attack lifecycle
- Benefit from SecIntel and advanced threat intelligence, including threat prevention policies protecting corporate assets, financial data, and business operations; employee protections; and secure customer information
What use cases do Juniper Threat Detection and Mitigation solutions support?
Juniper Threat Detection and Mitigation solutions are ideal for customers with business assets requiring active protection from advanced cyber threats in the following use cases:
- Campus
- Enterprise
- Data center
- Public, private, and hybrid cloud
- Service provider